From DevOps to DevSecOps: Embedding Security from Day Zero
Over the past decade, the evolution from DevOps to DevSecOps has transcended buzzwords it has become a strategic necessity. In 2025, forward-thinking organizations no longer view security as a final checkpoint in the development lifecycle.
Instead, they weave it into the very fabric of their workflows from Day Zero right from the first line of code. This proactive integration not only reduces vulnerabilities but also accelerates innovation, ensuring that speed never comes at the cost of security.
What does “Day Zero” security look like?
Embedding security from Day Zero means integrating security across every stage of the software delivery lifecycle not just at release time, but from the earliest design, coding, build, deployment and runtime phases. Key facets include:
1.Threat modelling and design-stage security: At the outset of a feature or system design, security risks are identified (e.g., data flows, trust boundaries, credential management) and mitigations are designed in.
2.Secure coding practices: Developers follow secure coding guidelines, avoid common weaknesses (e.g., input validation, injection, improper authentication) and use automated code scanning tools.
3.Continuous security scanning in CI/CD: Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), secrets scanning, Infrastructure-as-Code (IaC) scanning are integrated into CI/CD pipelines. For example, the pipeline might look like: build → test → security scan → deploy.
4.Infrastructure as Code (IaC) & platform security: Infrastructure defined as code must be scanned for misconfigurations, secrets, insecure defaults. Minimal container images, secure by default configurations help harden the platform.
5.Runtime monitoring & guardrails: Once deployed, runtime context matters. Which vulnerabilities truly matter depends on whether the service is publicly accessible, exposed to attack, has known exploit. Security teams should use context to prioritise.
6.Feedback loops & shift-right security: Security issues discovered in production feed back into dev and build pipelines so that issues are prevented in future.
7.Culture, training & shared responsibility: Development, operations and security teams collaborate, security is everyone’s job.
1.Threat modelling and design-stage security: At the outset of a feature or system design, security risks are identified (e.g., data flows, trust boundaries, credential management) and mitigations are designed in.
2.Secure coding practices: Developers follow secure coding guidelines, avoid common weaknesses (e.g., input validation, injection, improper authentication) and use automated code scanning tools.
3.Continuous security scanning in CI/CD: Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), secrets scanning, Infrastructure-as-Code (IaC) scanning are integrated into CI/CD pipelines. For example, the pipeline might look like: build → test → security scan → deploy.
4.Infrastructure as Code (IaC) & platform security: Infrastructure defined as code must be scanned for misconfigurations, secrets, insecure defaults. Minimal container images, secure by default configurations help harden the platform.
5.Runtime monitoring & guardrails: Once deployed, runtime context matters. Which vulnerabilities truly matter depends on whether the service is publicly accessible, exposed to attack, has known exploit. Security teams should use context to prioritise.
6.Feedback loops & shift-right security: Security issues discovered in production feed back into dev and build pipelines so that issues are prevented in future.
7.Culture, training & shared responsibility: Development, operations and security teams collaborate, security is everyone’s job.
Latest Trends in DevSecOps (2025)
Here are some of the leading trend's organisations should be aware of in 2025:
1.AI/ML-driven security automation
1.AI/ML-driven security automation
- Use of large language models (LLMs) and graph-based machine learning to predict vulnerabilities, misconfigurations, anomaly detection.
- On the flip side, attackers are also using AI to orchestrate more advanced attacks, so defenders must stay ahead.
2.Tool consolidation and platformisation
- Many organisations find themselves dealing with tool sprawl (too many security tools, each with silos). In 2025 the move is toward unified DevSecOps platforms that integrate security into the dev toolchain rather than bolt-on.
3.GitOps & Infrastructure as Code (IaC) security
- GitOps (using Git as single source of truth for infrastructure and application state) continues to gain traction. Secure IaC, minimal images, version-controlled configs are front-and-centre.
4.Zero-trust and runtime context awareness
- Security prioritisation is shifting from just “vulnerability count” toward runtime context: is the asset internet-facing? Is there an exploit in the wild? Does the service handle sensitive data?
5.Platform Engineering & internal developer platforms (IDPs) with security built-in
- Organisations are building internal developer platforms so that developers can self-serve, but these platforms must have guardrails: security, compliance, environment provisioning baked-in.
6. Focus on SMEs and maturity gaps
- Although many large enterprises are moving ahead, SMEs still face challenges in adoption: technical complexity, resource constraints, cultural resistance.
Practical Roadmap: How to Embark on DevSecOps from Day Zero
Here’s a practical step-by-step roadmap that you can use to embed security from Day Zero within your organisation’s DevOps pipeline.
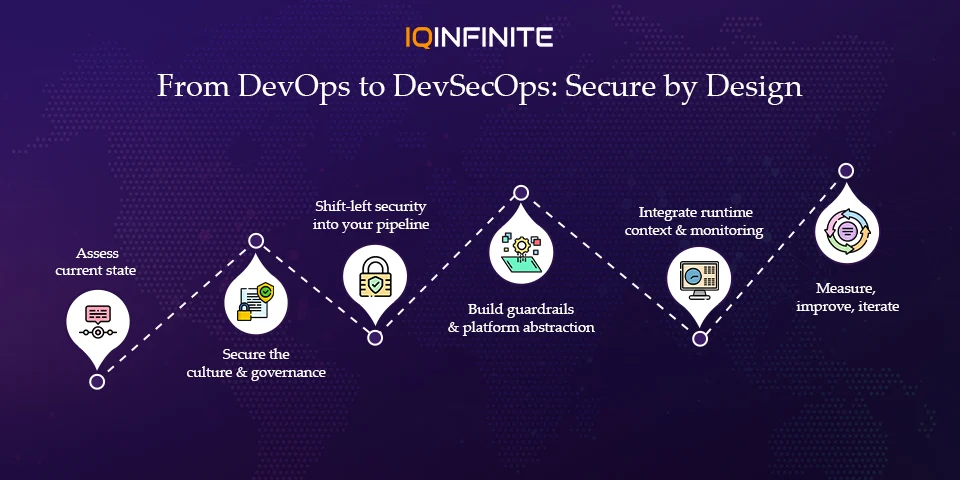
Step 1: Assess current state
Step 1: Assess current state
- Map out your current development, operations and security workflows.
- Identify where security is currently applied (e.g., only at QA or only pre-production) and where gaps exist.
- Evaluate tooling: Do you have SAST/DAST/SCA/IaC scanning? Are they automated? What is your vulnerability remediation time?
Step 2: Secure the culture & governance
- Establish that security is a shared responsibility (development, operations and security teams) rather than a silo.
- Define your security policy/guardrails early: coding standards, dependency management, secrets management, infrastructure configuration.
- Train developers on secure coding, threat modelling, dependency hygiene.
Step 3: Shift-left security into your pipeline
- Integrate SAST, SCA (software composition analysis), secrets scanning in your CI pipeline so that code is automatically scanned during build/commit stage.
- Introduce IaC scanning for your infrastructure templates (Terraform, Pulumi, Ansible etc).
- Use minimal container images and scan container images for vulnerabilities.
- Define quality/security gates: e.g., builds fail when critical vulnerabilities are found or unauthorized secrets detected.
Step 4: Build guardrails & platform abstraction
- Build an internal developer platform or self-service environment where developers can deploy infrastructure/code themselves but within predefined, secure guardrails. This reduces reliance on ad-hoc click-ops and increases consistency.
- Store all deployment, infrastructure state in Git (GitOps) and make those repositories subject to security review and scanning.
Step 5: Integrate runtime context & monitoring
- Use runtime context (is asset internet-facing, active exploit, etc) to prioritise vulnerability remediation.
- Deploy continuous monitoring of your production environment for anomalies, misconfigurations, drift in IaC, container run-time threats.
- Feed findings back into dev pipelines (shift-right) so that lessons learned improve code/infrastructure for future.
Step 6: Measure, improve, iterate
- Define KPIs: e.g., mean time to detect (MTTD) vulnerabilities, mean time to remediate (MTTR), number of blocked builds due to security, percentage of deployments with no critical findings.
- Conduct regular “security retrospectives” after incidents or near-misses.
- Continuously evolve tooling and processes: for example, adopting AI/ML based security scanning and anomaly detection as the technologies mature.
Common Pitfalls & How to Avoid Them
- Tool sprawl and disconnected tooling: Having many security tools each scanning parts of the pipeline but without integration creates blind spots and inefficient workflows. Aim for unified, integrated pipelines.
- Late security involvement: If security is still only engaged at release time, many vulnerabilities will already be baked in. Shift-left early.
- Over-reliance on manual reviews: With rapid delivery cycles, manual security gates become bottlenecks. Automate what you can and prioritise what requires human review.
- Ignoring runtime risk context: Not all vulnerabilities are equal. Without context (exposure, exploitability), you may waste time fixing low-impact issues while high-impact remain open.
- Culture resistance: If developers view security as a blocker rather than enabler, adoption will stall. Invest in training and communication.
- Underestimating infrastructure/code drift: Even secured code and infrastructure at release time can drift or be misconfigured later. Runtime monitoring and IaC scanning are essential.
Why It Matters for Your Business
- Reduced risk and cost: Catching and remediating vulnerabilities earlier in the cycle is significantly cheaper and less damaging than dealing with production breaches.
- Faster time to market: Counterintuitively, embedding security early can accelerate delivery by avoiding late-stage security bottlenecks and re-work.
- Enhanced trust and compliance: Regulators, customers and partners increasingly demand secure, auditable, compliant systems. DevSecOps helps you demonstrate that.
- Competitive advantage: In 2025 and beyond, organisations that can deliver innovations fast and safely will stand out. Secure software becomes a business differentiator.
Conclusion
The evolution from DevOps to DevSecOps marks a fundamental shift in how software is developed, deployed and operated. Embedding security from Day Zero isn’t merely a technical change it’s a cultural, organisational and process transformation. By shifting left, automating key security checks, integrating runtime context, building guardrails and fostering a shared security mindset, organisations can deliver faster and safer software.
If you begin today, you’re not just protecting your systems you’re enabling your organisation to innovate with confidence.
If you begin today, you’re not just protecting your systems you’re enabling your organisation to innovate with confidence.
